See this article in another language:
If you ask anyone what the most important principle was in learning the net+ course, most people will point to the OSI model. Concept learning of this model is very practical for people and you can learn many concepts better by learning it.
Actually, I didn't want this article to be that long and boring. For network+ topics, you may only need half of what I've described in the article below.
Even on the protocols of each layer that I explained in the article about it, you don't need to know much about these things and in many classes and trainings they only talk about it.
The reason I looked so closely at the OSI model is mainly because I wanted to share everything I knew with you. Also, as I explained to you in the introduction to the Network+ training, one of the goals of these educational articles is to learn more about myself and the course of discussions.
Due to the length of this article, I have prepared a list of its titles so that you can easily access each part of the article:
1.Introduction
2.What is the OSI model?
3.Components of the OSI model
3.1.Physical layer
3.2.Data link layer
3.2.1.Arbitration
3.2.1.1.CSMA / CD
3.2.1.2.CSMA / CA
3.2.2.Physical Addressing
3.2.3.Error Checking
3.2.4.Encapsulation/Decapsulation
3.2.5.Famous protocols of data link layer
3.2.5.1.PPP
3.2.5.2.ATM
3.2.5.3.Ethernet
3.3.Network layer
3.3.1.Routing
3.3.2.Logical Addressing
3.3.3.Error Detection
3.3.4.Encapsulation/Decapsulation
3.3.5.The famous protocols of the Network layer
3.3.5.1.IP
3.3.5.2.ARP
3.3.5.3.ICMP
3.3.5.4.IPsec
3.4.Transport layer
3.4.1.Segmentation
3.4.2.Flow Control
3.4.3.Error Handling
3.4.4.Segment Sequencing
3.4.5.Service Addressing
3.4.6.Famous protocols of Transport
3.4.6.1.TCP
3.4.6.2.UDP
3.5.Session layer
3.5.1.Famous Session layer protocols
3.5.1.1.NetBios
3.5.1.2.PPTP
3.5.1.3.PAP
3.6.Presentation layer
3.6.1.famous protocols of the Presentation layer
3.6.1.1.SSL
3.6.1.2.TLS
3.7.Application layer
3.7.1.Famous application layer protocols
3.7.1.1.FTP
3.7.1.2.http
3.7.1.3.POP3
3.7.1.4.SMTP
3.7.1.5.IRC
3.7.1.6.SSH
3.7.1.7.DNS
4.Network Admin & Engineering
Introduction - The need for computer networks
After the end of the world war, when the media war became more intense; The discussion about the remote transfer of data and information has become more important. The story started when spies operated in other countries and had problems when they wanted to send their information and findings.
For example, spies in Russia wanted to send information to intelligence agencies in America. The story here was that Moscow was far from America, and the story wasn't the only distance. Even the transfer of information should be done in such a way that spies do not get into trouble.
That is, in computer networks, like all other technologies, there was a military aspect in the beginning, and governments used this computer networking platform for espionage and other military applications. Among them, there were a number of government-affiliated companies that were responsible for the expansion of this platform.
Usually, when a technology is monopolized by a system, it becomes public after a few years and is available to people. This work is beneficial to governments and countries in two respects. First, when a technology is publicly available because more people are working on it; More growth is directed towards technology.
Second, governments release a technology to market when they have complete control over it, and by using it, they can spy on their own people or other countries and store their information.
Later, in countries like Iran, it became clear that the reason we were weak in some areas was that we were using an information transfer platform originally designed for espionage. For example, after a period of war in the Middle East, soldiers realized they shouldn't use smartphones.
The activation of GPS-equipped systems in wars could have irreparable consequences. Or in wars, the use of Internet systems can identify people's location. In a sense it can be said that when we use the Internet we are slaves to the information of developed countries such as the United States.
After some time, the Americans themselves realized a major challenge in computer networks. The story began when other sciences were advancing faster than the knowledge of computer networks. Indeed, because the government had kept the Internet as a monopoly and did not make its science available to the public.
That is, in general, before computer networking technology went public, it was only developed by a handful of companies like IBM, Xerox, and Intel. And these companies benefit greatly from the fact that this technology is not available to people.
The story was not only about the uniqueness of the technologies, each of the companies that were tasked with developing computer networks used their own standards and technologies to develop the network. As a result, the products of IBM companies could not be integrated with Intel.
The companies that worked exclusively and under government supervision on computer networks each had a technology to expand and connect the networks. Thanks to this technology, each company used its own network topology.
And based on this topology used by each company, the manufacturing company produced and marketed a number of parts and devices for itself. If you recall, one of the companies that had a monopoly on expanding computer networks was Xerox.
Xerox was a company that used Ethernet technology and BUS topology. In this article, we will talk about Ethernet and its various standards.
The OSI model
Due to the weakness of the networks, the government forced companies developing computer networks to use a single standard for data transmission in computer networks. ISO company, which is an enterprise in the field of global standards, decided to enter the field of network in 1970.
ISO or International Organization for Standardization, which you must know, has set standards for manufacturers in the field of many food structures, technologies and products. You must have heard the name of this company in many TV commercials.

This company specializes in the field of manufacturing and standard products. The ISO company designed a standard called OSI in the field of computer networks. The OSI model stands for Open Systems Interconnection model, i.e. the system connection model in general.
OSI is a hypothetical model consisting of seven layers where each of these layers has its own task and does its job. The word Interconnectedness means that there is an internal connection in this model and each level is connected with the two levels before and after it.
To simplify the explanation, each layer interacts internally with another layer or layers. The OSI model is exactly like a factory production line; That is, the output product of each layer is ready to be used as feedstock in the next layer.
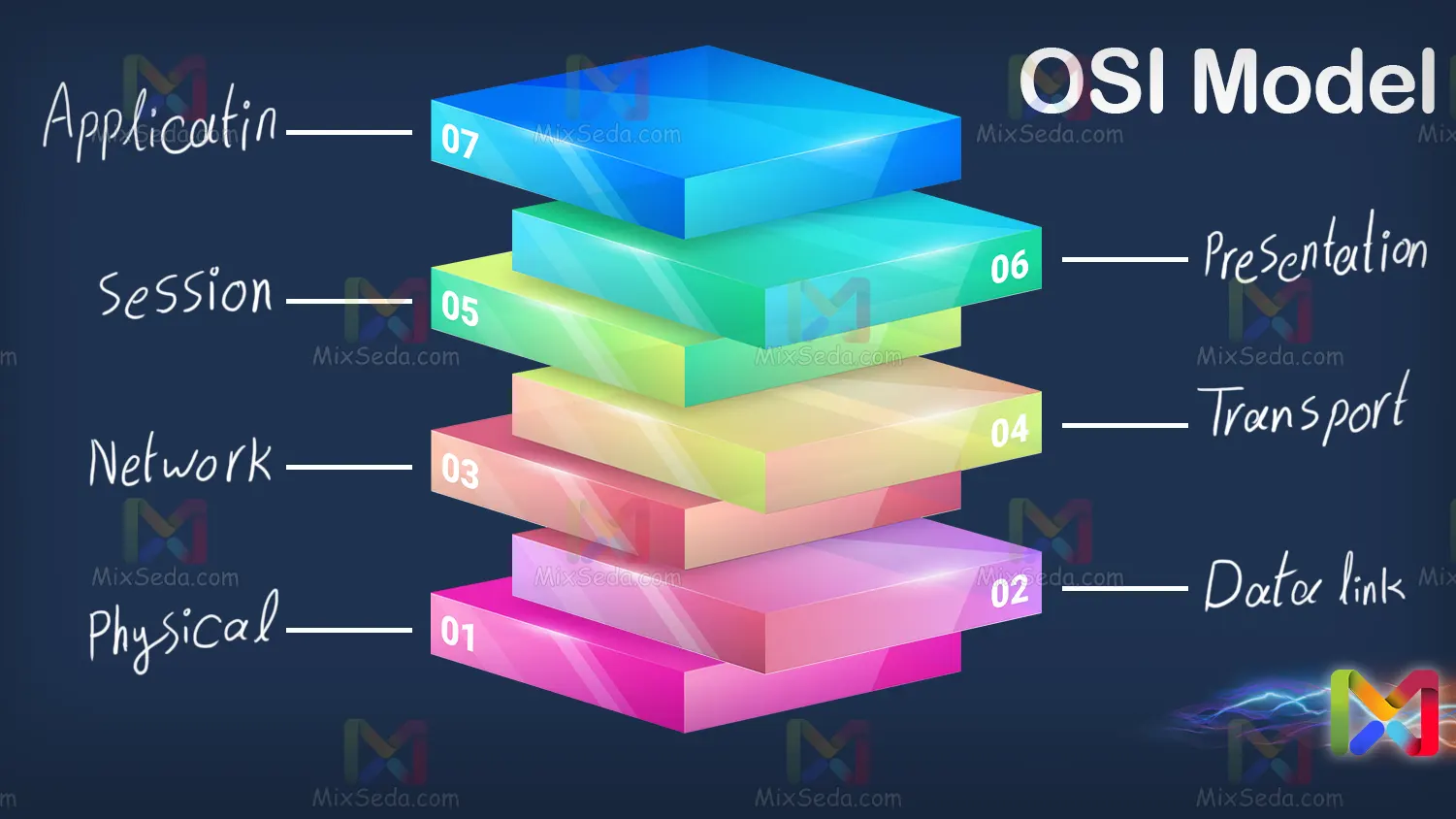
To better explain this issue, the OSI model is a hierarchical model. The philosophy of the OSI model was for manufacturers to produce and market their products based on the OSI model.
On the other hand, as an administrator and manager of a computer network, I also design and expand my own network based on this OSI model. Also, one of the reasons for such a model was to teach students about the network and its components.
Another reason was that if you would talk about a concept in the network, you could convey your exact meaning to the other party. For example, if you encountered a problem in your network, you could more easily convey your meaning to the other party using the OSI model.
Components of the OSI model
Well, we want to go to the different sections of OSI and explain each of these sections. OSI includes the following seven sections:
- First layer: Physical layer
- Second layer: Data link layer
- Third layer: Network layer
- Fourth layer: Transport layer
- Fifth layer: Session layer
- The sixth layer: Presentation layer
- The seventh layer: Application layer
You may see in some of your articles that the names of these layers have been translated into Farsi. Try to learn all the English concepts in the online world so that in the future when you want to read English articles you will understand their concepts.
In the layers of the OSI model, the closer the layers are to the application, the more understandable they are. The application is the level closest to the user. Before explaining each of the components of the OSI model, I would like you to familiarize yourself with what port and protocol mean.
Imagine me using Persian when I want to talk. If I want to communicate with another person, the other person must be able to communicate with me using the Persian language. This is exactly what protocol means.
In the computer world, computers with the same protocols can communicate with each other. If I speak English with someone; The person in front of me must know English to be able to answer me. So, so far, protocol is the common language between systems.
Imagine you want to enter a house, well, you definitely enter the house through the door. Your computer is like a house that has many doors for data and information to enter and exit. Each of these ports is called a port.
Ports are specific ports on a computer system created for data input and output. On a computer, each port has its own use. And every packet sent to your computer is received by its own port on your computer.
Physical layer
The first layer of the OSI model is the physical layer. Within network cables, signals are transmitted as voltage between computers. Network card interfaces receive these voltages and your computer's network card converts them into bits.
That is, the voltages that exist along the network cable are converted to 0s and 1s after this layer. In fact, for network cards, the algorithm is defined to convert the voltage to 0 and 1 in a certain period of time.

It's a bit difficult to explain the conversion of digital signals to bits and vice versa, but you can read about polar and unipolar encodings for a better understanding. In network cards, several voltage levels are usually used to display binary values.
For example, imagine that voltages from +3V to +5V are considered bit 1 and voltages from -3V to -5V are considered bit 0 in network adapters. In fact, Manchester is used for data transfer in computer networks.
Of course, no one will ask you about this code, but if you're interested in network card circuitry and how to transfer 0s and 1s in computer networks, you can research Manchester and the IEEE 802.3 standard.
Such network cards can convert digital signals into digital data using a voltmeter at certain intervals of time.
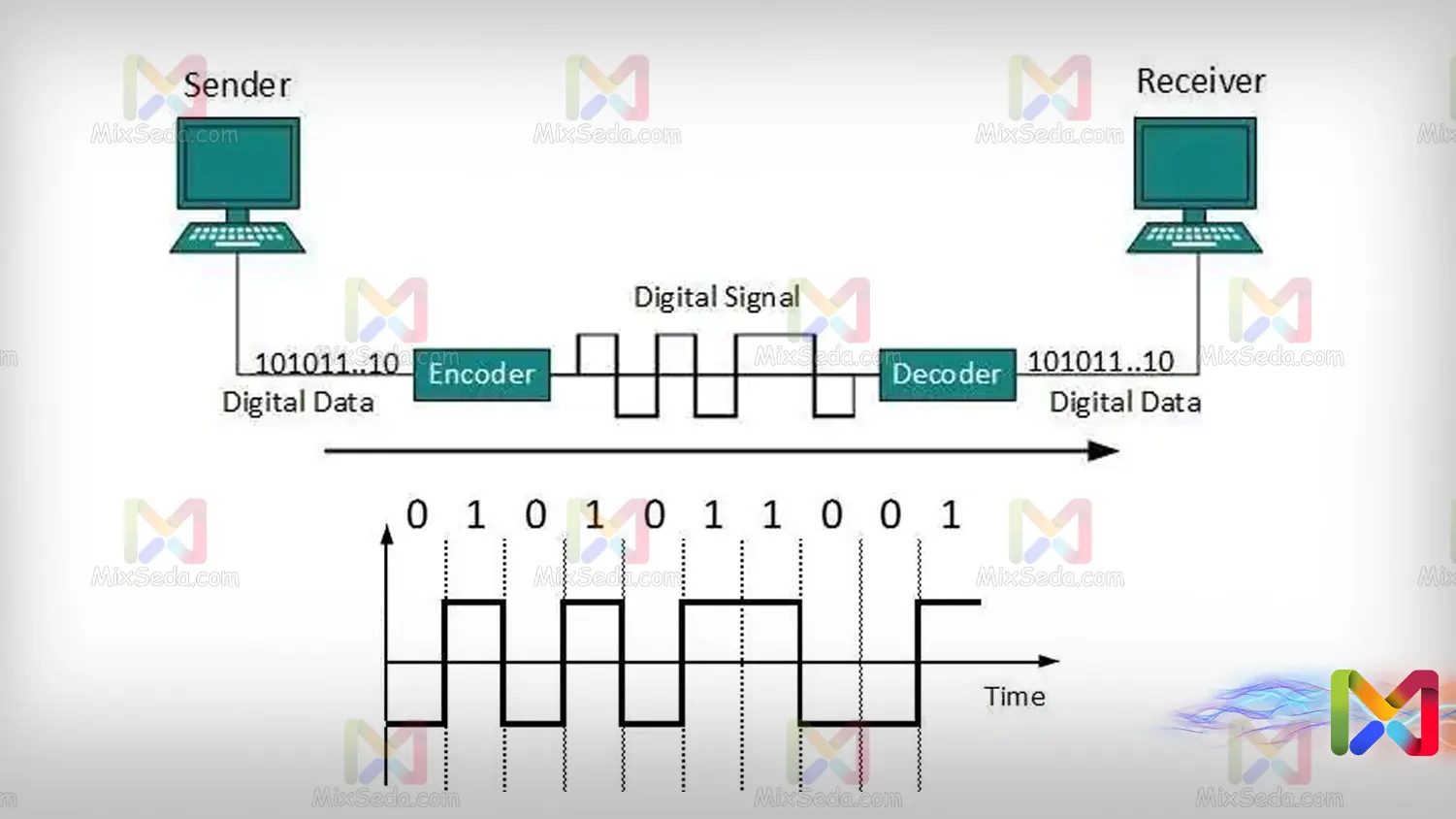
Data link layer
The tasks of the second layer of the network include 4 important parts:
Arbitration
If you remember, when we were discussing computer network topologies, we explained that we have a concept called collision, which means interference and coincidence of data with each other.
Well, no measures have been taken in the physical layer of the network to prevent collisions in the network. Instead, the next layer, which is the data link, has an important job called arbitration, which is supposed to resolve the collision.
CSMA / CD
One of the methods of arbitration was the CSMA/CD mechanism designed by Xerox. This mechanism was designed in such a way that before sending information from a computer, it checks the medium and if it is down, sends the information to the destination computer.
I would like to explain this problem easier, this mechanism monitors the network and if the network is silent and no other computer sends data, it transfers its data over the network.
One possibility that existed in the interim was for two computers to control the media at the same time and upon realizing that the network is down, send the information at the same time; In this case, we will review Collision.
For this reason the mechanism has been modified so that the first computer that detects a collision in the network informs all computers in the network that a collision has occurred. The signal that is sent to inform about the occurrence of collisions in networks is called a jam signal.
After receiving the jam signal from the computers, all computers wait for a random amount of time and run the CSMA/CD process again. It means to check if the network is down again and if it is free, they will send the information.
Since this time is randomly determined between computers, it is very unlikely that the random time of two computers will be equal to each other and the collision will happen again. There was a chance of collision in this mechanism, but this mechanism reduced the probability of collision.
Indeed, CD at the end of the name of this mechanism means Collision Detection. That is, a mechanism for detecting collagen in the network.
CSMA / CA
The IBM company designed another mechanism called CSMA/CA, i.e. Collision Avoidance, and claimed for the first time that collision and interference do not occur in computer networks. (This mechanism has been called Token Passing.)
IBM used ring topology in its structure and designed hardware devices called MAUs, which actually didn't look like a ring topology, but these MAU devices changed the topology to ring.
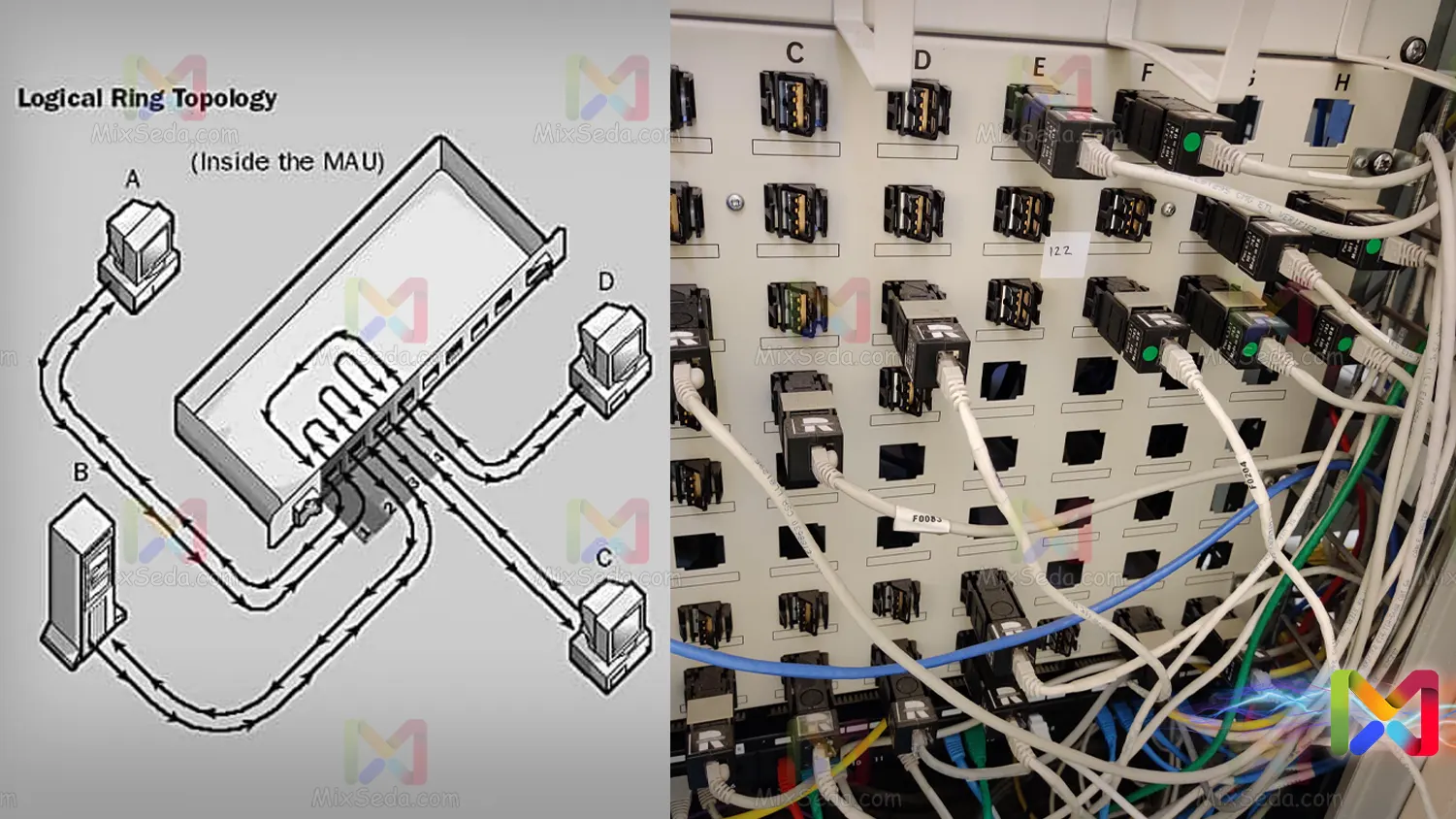
The CSMA/CA mechanism worked in such a way that there was a specific flow called a token on the network. The token was actually a license to exchange information and there was only one token in the network. Now imagine that a computer is going to exchange data for hours.
For this case, IBM had set a certain amount of data exchange. That is, a computer had no right to take possession of the token and use it as much as it wants. After exceeding the information exchange limit, the computer should hand over the token to other computers in the network.
Not only was there a limit on the amount of data transferred in this mechanism, but there was also a time limit on having the token. So each computer, when it wanted to send information, would check the media and if no one had the token, it would start transferring the information.
This mechanism was Collision Free which means you will not have any collision and interference in computer networks using this mechanism. But the interesting thing was that, contrary to IBM's ideas, due to the difficulty of implementing this structure and its high cost, this mechanism was not well received.
Regarding the arbitration and its modalities, the following table can be used:
|
Row |
Manufacturer |
Technology |
Topology |
Arbitration |
Device |
|
1 |
Xerox |
Ethernet |
BUS / Star |
CSMA/CD |
HUB |
|
2 |
IBM |
Token ring |
Ring |
Token passing |
MAU |
So, so far, the first task of Data link layer is Arbitration.
Physical Addressing
One of the important tasks of the data link layer is to generate and monitor the physical address of packets in the network. In the OSI model, neither layer should interfere with each other's work. Based on this, the data link layer basically doesn't notice the product being reached by the network layer.
In effect, the data link layer should receive the products of the network layer, perform its activities on it, and deliver it to the physical layer. Or take the physical layer product and deliver it to the network layer after performing its functions.
Now, one of the tasks of the Data link layer is to transfer all the product received from the higher layer, Network, into a specific container called payload and package it. Just like a parcel post you send out in the real world.
Well, this postal package needs the recipient and sender address so that it can be sent to the destination computer. So the data link layer adds a source address and a destination address and a bunch of other stuff on each packet. These items are added to each package in the header section.
Also, every package in computer networks has a footer or trailer. Before each packet is sent, everything in the header section is converted into code by a function called CRC (cyclic redundancy check).
As a result of the CRC function, we will have a value called FCS, which is also called CRC Checksum. Now this value of FCS or CRC Checksum is written in the Trailer section of each package.
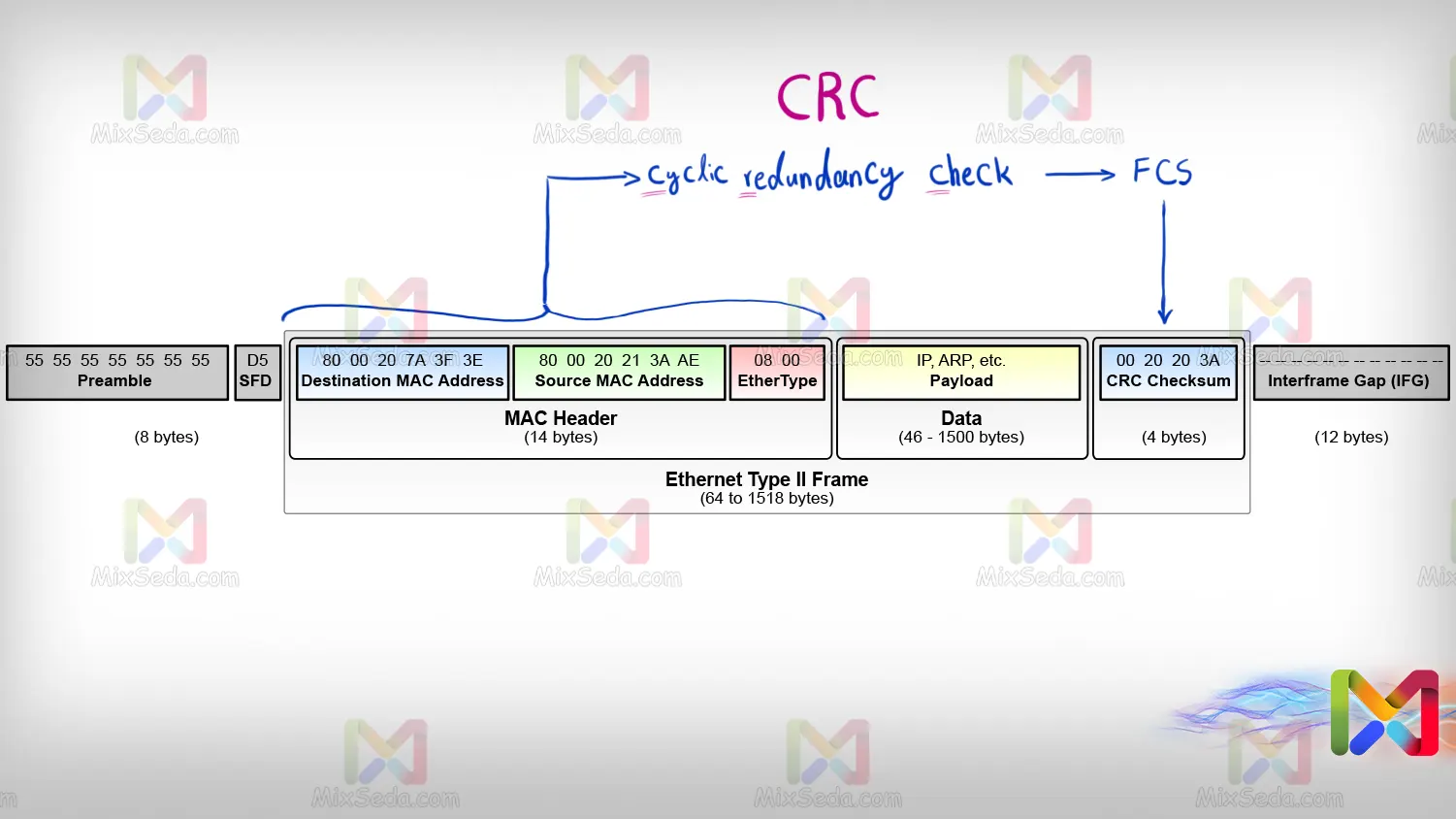
I really wanted to explain all the components of the header to you here, but I've come to the conclusion that this article is getting too long. Other than that, there are many specialized concepts and it is difficult to explain them with the knowledge you currently have from reading this article.
When the packet reaches a computer, in the second layer, before anything is done to it, it checks if the packet was sent correctly. That is, the FCS value is again included in the reverse CRC function, and if its value equals the header, it is clear that the packet has successfully reached its destination.
If the package is not sent successfully, the desired package will be discarded by the computer that received it. Another point is that the physical address is different in different technologies. For example, in Ethernet technology, the physical address is the same as the MAC address or the media access control address.
In ATM technology, which we will learn more about later, the physical address is defined by two concepts, VPI and VCI, which you may have seen when configuring telecommunication modems.
Error Checking
The data link layer performs the error checking task in two ways. One such method is called LLC or Logic Link Control. LLC is responsible for the integration and coordination of the frames. In short, LLC checks that the package format is correct.
I want to explain more easily, packets are not sent like this out of order in the network world. All packets that exist in a network follow a set of standards and LLC is logically responsible for monitoring these standards.
The second method for error checking in the data link layer is physical. In the second method, the physical address of each packet is checked so that the data link layer concludes that the packet has successfully reached its destination.
Encapsulation/Decapsulation
On the sender's side, every packet passing through the data link layer undergoes the encapsulation process before being sent. On the destination computer side, each received packet is first decapsulated before any processes are started on it.
The product of the data link layer after encapsulation is frame. That is, in practice, the data link layer receives the network layer packet or payload and converts it into a frame, or it receives the frame and delivers it to the network layer as a packet.
Famous data link layer protocols
PPP
The PPP protocol, which stands for Point-to-Point, is a protocol in the second layer of the network whose job is to transfer data and information point-to-point. For some reasons, the PPP protocol is used in media where bandwidth is not limited.
For example, this protocol is implemented over physical fiber optic links, serial cables, and other high-speed media. PPP protocol itself uses another protocol called LCP or Link Control Protocol for its function.
In addition, the PPP communication protocol provides good services to network operators, one of which is the management of link quality and established communication.
Among other features and characteristics of the PPP protocol, we can mention the need for authentication in it. The existence of such a feature increases the security of information exchange.
The first time this protocol was presented by the IEEE organization (Institute of Electrical and Electronics Engineers), but the company Cisco, modifying this protocol, provided an exclusive version of it called HDLC.
Well, in many cases, HDLC is not used because many devices in your network may not be able to understand it, but usually in connections where you are using Cisco products on both sides of the case, it is definitely better to use the HDLC protocol.
In the future, we will talk more about applications and how to set up this protocol, and for now, I wanted you to be familiar with this protocol.
ATM
ATM protocol or asynchronous transfer mode is one of the protocols designed for fast transfer of a certain type of data. This protocol is used to transfer data such as audio and video.
In fact, the reason to use this protocol is how it works. The ATM protocol divides digital data into 53-byte segments and sends them on a medium. Each of these parts is called a cell.
In reality, each 53-byte cell contains 48 bytes of data or payload and 5 header bits. Then each piece of digital data is processed separately and sent sequentially. We can talk for hours about the mechanism of this protocol, but for now what you should know is limited to applications of the ATM protocol.
The structure and mechanism of the ATM protocol has made routers not involved in processing the different sizes of the sent packets. Because of this, the speed of processing and data transfer increases on the basis of this protocol.
So that the standard transmission speed of this technology on fiber-optic cables is about 155 megabytes per second, but in ATM networks the data transmission speed can be increased up to 10 gigabits.
Ethernet
The Ethernet protocol is a standard protocol for use in computer networks, usually used in LAN and MAN networks. Computers that exchange information using the Ethernet protocol convert data into smaller pieces called frames.
Frame itself includes other parties such as LLC and MAC. We will talk about MAC or Media Access Control in detail in the next article. LLC or Logic Link Control is responsible for the integration and synchronization of the frames.
The Ethernet protocol generally operates in two data link and physical layers of the OSI model. In terms of speed, the Ethernet protocol has three standards, which include Standard Ethernet, Fast Ethernet and Gigabit Ethernet.
Standard Ethernet was the first Ethernet standard capable of transferring data at a speed of 10 Mbps. Well, this amount of speed was definitely not enough for even a small local area network.
For this reason, the IEEE organization worked on the IEEE 802.3 standard and the result was IEEE 802.3u and IEEE 802.3z, which we know as Fast Ethernet and Gigabit Ethernet.
Gigabit Ethernet (IEEE 802.3z) is the third generation of Ethernet that is widely used in today's networks. You will be able to transfer information up to 70 km through this standard. Of course, this standard is an expensive standard.
Fast Ethernet (IEEE 802.3u) is the second generation of Ethernet and, as the name suggests, this standard has a high speed of data transmission. So that the standard speed of Fast Ethernet reaches 100Mbps. Of course, compared with Gigabit Ethernet, this standard cannot transfer data over long distances.
As a standard, Fast Ethernet has the ability to transfer data up to 10 kilometers, which can almost be said to be 14% of the Gigabit Ethernet standard in data transmission.
Network layer
Routers and network devices responsible for routing operate in this layer. The reason for this is that all these devices work based on the IP address.
In fact, we have two types of addresses in computer networks, one is physical address, which includes MAC address as I said, and the other is logical address, which includes IP address.
It can be said that almost everyone is familiar with the IP address, but I will tell about them separately.
The tasks of the third layer of the OSI model include the following:
- Routing
- Logical Addressing
- Error Detection
- Encapsulation/Decapsulation
Of course, there are other activities in the Network layer that we won't mention right now. Now we want to explain each of these cases so that you can understand more precisely what happens in the third layer of the network.
Routing
To route means to route. It is possible for a packet to reach its destination among network devices multiple times. For example, when you move a file across the internet, the file might be passed between dozens of network devices to reach its destination.
Just as in the real world you have the ability to take different paths to reach your destination, a packet in the networked world can also have different ways to reach its destination.
Routing means that a packet chooses the best way in the network to reach its destination. You can view the default routes of a system using the route print command in the Windows Terminal (CMD).
In the network layer, a virtual circuit is created between the source and the destination and the sent packets move to the destination using this virtual circuit. To explain a little better, logical paths are created in the network layer to send packets.
Logical Addressing
Logical addressing is addressing using the IP or Internet protocol. This type of addressing has similarities to physical addressing, but MAC address is used in physical addressing.
The third layer of the OSI model also has a header like the data link layer. In this layer, the logical address of the source and destination of each packet is added to the header section in IPv4 and IPv6.
Error Detection
You could say that in the data link layer of our network, we have done the error detection process once and why should we repeat this process? The reason is that the process of detecting errors that occurred in the lower layer is different from detecting errors that occur in the network layer.
We said that the data link layer lacks the power to understand the higher layers and just puts what it receives from the network layer into a specific format called a payload and adds other elements to it.
Therefore, in the data link layer, it is practically not possible to control the source and destination IP addresses of each packet.
Encapsulation/Decapsulation
In the third layer, like other OSI layers; After performing the operations and tasks of each layer, the encapsulation and decapsulation process is performed and then the data is transferred to higher or lower layers. As we said, the data link layer knows this information as a payload.
As we explained, different OSI layers don't interfere with each other's work, so the data link layer isn't literate enough to read the third layer's payload, nor is it allowed to interfere with the Netwprk layer.
Popular Network layer protocols
IP
IP stands for Internet Protocol. The most important task of the IP protocol is to route and specify the origin and destination of a packet. IP, like many other protocols in the network, has different versions and standards.
You must know that there are two versions of the IP protocol in the world called IPv4 and IPv6. All hosts on the network need a logical address and a physical address.
The logical address or logical address used to send each packet is IP. Just as in the real world it is not possible for two houses to have the same zip code, we will never have the same IP addresses in a computer network.
Some of the IP addresses are local or some are global or static. Local IP addresses are used in local networks. Typically, global IPs are provided for servers that are supposed to continuously provide services to users around the world.
The IP version 4 address contains 32 bits or 4 octets, which is 8 bits separated by a period. Also, the IP address itself includes two parts: Net ID and Host ID.
In a separate article, I explained the Internet Protocol, which I suggest you read for a better understanding of subnet mask and IP address types.
ARP
ARP or Address Resolution Protocol is actually responsible for looking up the MAC address of a specific IP address. Imagine you want to connect to a server; For that, you need to have the IP address of the server you want to connect to, but never use the MAC address to connect to it.
Meanwhile, your computer has to send a series of packets to connect to the target server in order for your connection with that server to be established. When these packets want to pass through the second layer of the network, i.e. the data link, this layer must include the physical address of the source and destination in the header section.
Well, the important question is: How does your computer know the MAC address of the destination it wants to send a packet to?
Here, your computer obtains the physical address of the target computer using the ARP protocol and as a result, the desired packet is sent.
Imagine that two computers want to exchange information over a network and one of these computers has an IP from the other computer. Before sending the packet to the second computer, the first one first checks a table called ARP Table to see if the MAC address of the second computer is present or not.
If these two computers have already exchanged information with each other, each computer has stored the other computer's MAC address and IP address in the ARP table.
If the second computer's MAC address did not exist in the ARP table; The first computer sends a packet over the network called an ARP request. In this packet, which is sent to the second computer's IP address, the broadcast MAC address is used instead of Dst MAC or the destination MAC address.
Since the first computer doesn't know the second computer's MAC address, Ver needs its MAC address to send each packet to the other computer, so instead of the destination MAC address, it uses the address FF:FF:FF:FF :FF:FF , which is called Broadcast MAC Address. they say.
All computers in the network receive this packet and when the packet reaches the third level of each of these computers, the logical address of these packets is checked. Therefore, if there is a computer on the network other than the destination computer, each of these computers will drop the sent packets.
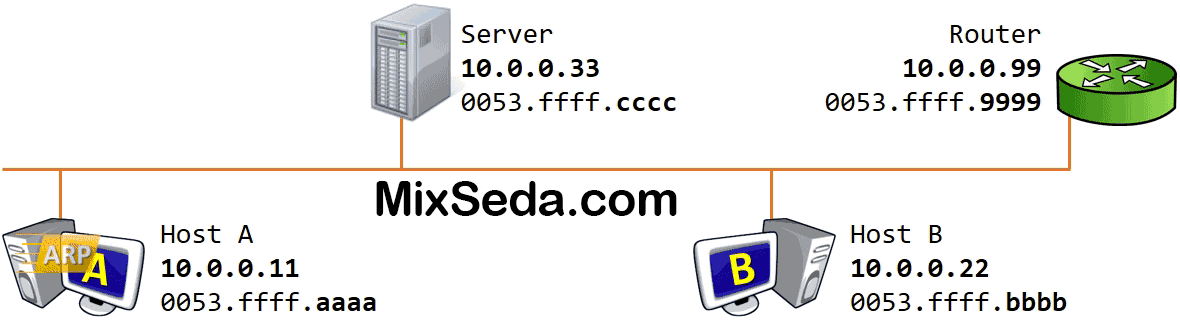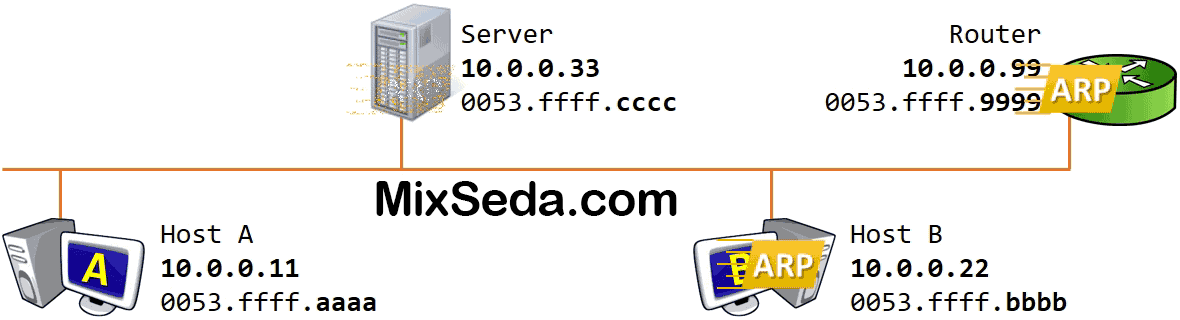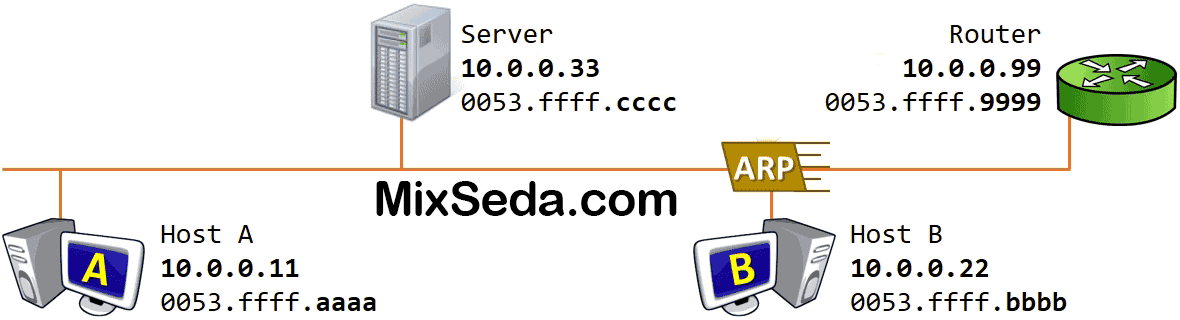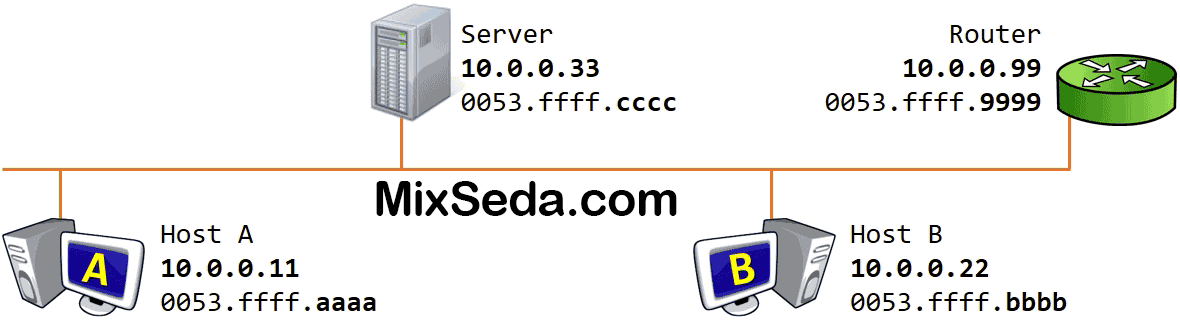
But when the ARP request reaches the target computer, considering the logical address of this computer is in the network layer; This computer sends a packet called ARP replay to the first computer. In this packet, the second computer enters its MAC address for the first computer.
In fact, when the first computer sent the ARP request, it had sent the MAC Src or MAC address of the source to the second computer, and when the second computer wanted to send the ARP replay, it knew exactly which computer it should send the packet to. .
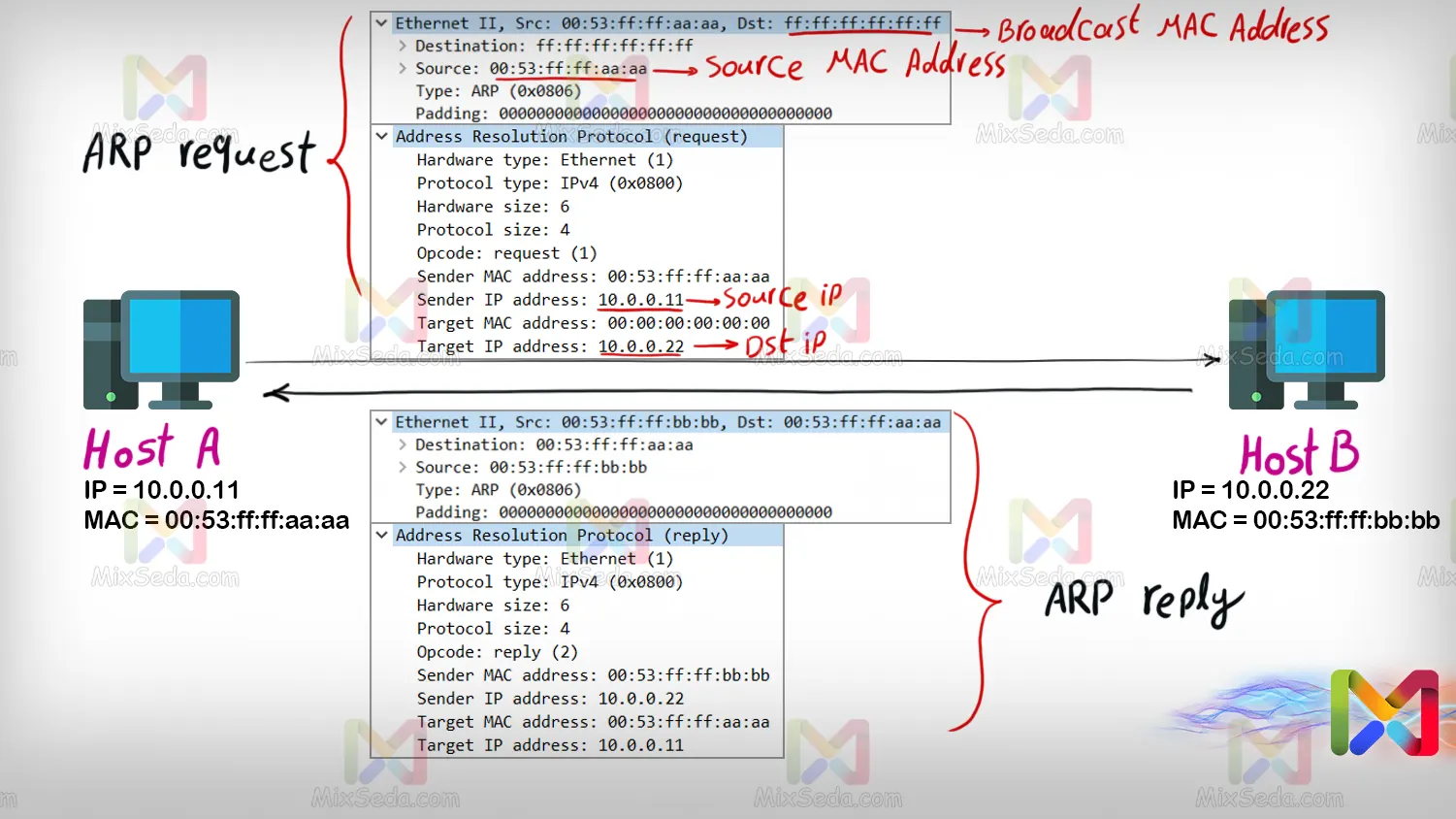
When the ARP playback reaches the first computer; Both computers have each other's MAC address and IP address, so they complete their ARP table so that this process doesn't have to be repeated on the next exchange of information.
The ARP protocol has many advantages for computer networks, but it also has disadvantages. Of course, most of these disadvantages are brought up in discussions related to network security. For example, in the ARP protocol, there is no system and mechanism for measuring the accuracy of ARP playback.
In other words, if a computer sends an ARP Replay to a computer that has sent an ARP Replay for unknown reasons over the network, the computer cannot verify that the information sent is correct.
Or hackers use attacks called ARP Spoofing or ARP Poisoning in computer networks, which you can learn more about in security courses.
ICMP
ICMP or Internet Control Message Protocol is one of the most important network layer protocols. This protocol is used to verify the connection and signal the line or the non-arrival of a packet at the destination.
The discussions on the ICMP protocol are very extensive and I will limit myself to explaining here how this protocol works in computer networks.
The ICMP protocol is responsible for sending different packets in the network and each of these ICMP packets conveys different concepts to the recipient based on the type and code they contain.
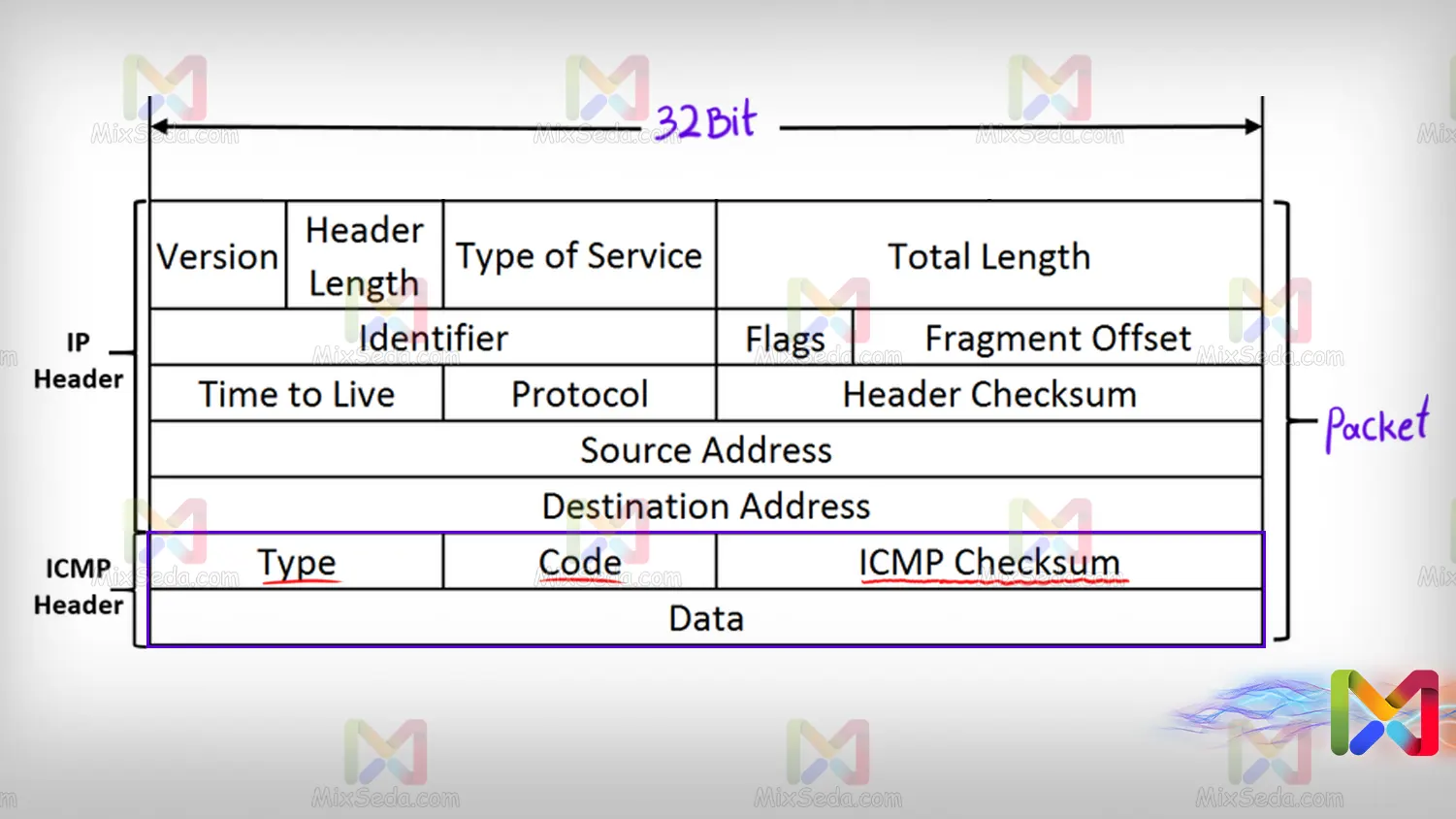
In general, these packets in computer networks include three main parts:
- Type
- Code
- Checksum
The Type section in each packet indicates the purpose for which this message was sent over the network. Sometimes a specific type of packages can have different types that the code distinguishes them from each other.
As the name suggests, the Checksum section is sent in each packet to confirm the correctness of sending the Type and Code sections in each packet.
The table below shows the types and codes of the ICMP protocol:
|
Description |
Code |
Type |
Type Number |
|
Echo reply |
0 |
Echo Reply |
0 |
|
Reserved |
- |
Reserved |
1 |
|
Reserved |
- |
2 |
|
|
Destination network unreachable |
0 |
Destination Unreachable |
3 |
|
Destination host unreachable |
1 |
||
|
Destination protocol unreachable |
2 |
||
|
Destination port unreachable |
3 |
||
|
Fragmentation required, and DF flag set |
4 |
||
|
Source route failed |
5 |
||
|
Destination network unknown |
6 |
||
|
Destination host unknown |
7 |
||
|
Source host isolated |
8 |
||
|
Network administratively prohibited |
9 |
||
|
Host administratively prohibited |
10 |
||
|
Network unreachable for ToS |
11 |
||
|
Host unreachable for ToS |
12 |
||
|
Communication administratively prohibited |
13 |
||
|
Host Precedence Violation |
14 |
||
|
Precedence cutoff in effect |
15 |
||
|
Source quench (congestion control) |
0 |
Source Quench |
4 |
|
Redirect Datagram for the Network |
0 |
Redirect Message |
5 |
|
Redirect Datagram for the Host |
1 |
||
|
Redirect Datagram for the ToS & network |
2 |
||
|
Redirect Datagram for the ToS & host |
3 |
||
|
Alternate Host Address |
- |
Alternate Host Address |
6 |
|
Reserved |
- |
Reserved |
7 |
|
Echo request (used to ping) |
0 |
Echo Request |
8 |
|
Router Advertisement |
0 |
Router Advertisement |
9 |
|
Router discovery/selection/solicitation |
0 |
Router Solicitation |
10 |
|
TTL expired in transit |
0 |
Time Exceeded |
11 |
|
Fragment reassembly time exceeded |
1 |
||
|
Pointer indicates the error |
0 |
Parameter Problem: Bad IP header |
12 |
|
Missing a required option |
1 |
||
|
Bad length |
2 |
||
|
Timestamp |
0 |
Timestamp |
13 |
|
Timestamp Reply |
0 |
Timestamp Reply |
14 |
|
Information Request |
0 |
Information Request |
15 |
|
Information Reply |
0 |
Information Reply |
16 |
|
Address Mask Request |
0 |
Address Mask Request |
17 |
|
Address Mask Reply |
0 |
Address Mask Reply |
18 |
|
Reserved for security |
- |
reserved |
19 |
|
Reserved for robustness experiment |
- |
reserved |
20-29 |
|
Information Request |
0 |
Traceroute |
30 |
|
Request Extended Echo (XPing - see Extended Ping (Xping)) |
0 |
Extended Echo Request |
42 |
|
No Error |
0 |
Extended Echo Reply |
43 |
|
Malformed Query |
1 |
||
|
No Such Interface |
2 |
||
|
No Such Table Entry |
3 |
||
|
Multiple Interfaces Satisfy Query |
4 |
Really, if I want to explain all of the above things, except I don't know many of these things, this article is going to be very long. I will explain the ICMP protocol separately later.
One of the most common uses that every person tries to communicate is ping. The ping tool is one of the tools that uses the ICMP protocol to measure the connection between the source and destination.

IPsec
The IPsec protocol or IP security, as the name suggests, is a protocol for setting up secure, encrypted communications between computers. Actually, IPsec is not a single protocol and consists of several other protocols.
This protocol is usually not explained in network basics, it is basically related to security and network. You must be familiar with VPNs. The definition of VPN might be a little different than you think.
VPN or virtual private network in networks like the Internet allows you to connect from one public network to another private network and exchange data between your computer and other computers in the private network. Just as if you were directly connected to a private network.
Imagine you have activated a VPN on your computer; In this case, a secure tunnel is formed between you and the VPN servers you are using. So every packet you send is first sent to the VPN server and then moves to the destination.
One use of the IPsec protocol is to use it to set up a VPN. Additionally, other uses of IPsec include encrypting information on the network, building security for routers that route across the Internet, or for authentication.
We will discuss IPsec and its structure and what protocols it includes in the future. What you need to know at this stage is that the IPsec protocol works at the network level and its job is to create a secure connection between workstations.
Transport layer
This layer is responsible for logical communication such as Connection Oriented (direct connection) or Connection Less (no connection).
This layer is responsible for important tasks in the network, and among the tasks of this layer, the following can be mentioned:
- Segmentation
- Flow Control
- Error Handling
- Segment Sequencing
- Service Addressing
- Multiplexing
Of course, explaining all these things is a bit difficult, but you will get to know them thoroughly in the CCNA courses.
Segmentation
Segmentation is the first thing that happens after information moves from the Session layer to the Transport layer. In the real world, for better management, the class is divided into smaller groups, or in all countries it is divided into different provinces and states for better country management.
In computer networks, in the transport layer, information is broken down into smaller pieces, each of which is called a segment.
Flow Control
In the network we have a memory called Buffer, which acts as a queue for the created segments. Imagine your computer can't send a packet due to network congestion. Or there is interference in the network and your computer is unable to send packets over the network.
In this case, all segments that will be sent to lower levels in the future are stored for a while in the Buffer section. Something doesn't have to happen to the media to use Buffer.
For example, if the amount of information sent from the level above this level is large, this information is buffered for better sending.
Error Handling
Error handling in the transport layer checks whether all segments sent in the network have reached their destination. Imagine a message has reached the transport layer in the session layer.
In this case, the desired message is split into several segments and then sent to lower levels. When the receiving-side transport layer receives these segments, it must have all of them in order to produce the initial message and deliver it to the receiving session layer.
Error handling is a mechanism for error control, where after sending each packet, the computer waits for confirmation that it has arrived.
Segment Sequencing
Some people think that when you send a series of packets across the network, these packets will reach their destination in exactly the same order they were sent. But for various reasons, such an event does not occur in computer networks.
The order of segments arriving at their destination can be swapped. In this case, we will need a mechanism that corrects the order of these received segments for us.
For example, they give you messed up pages of a book and ask you to fix this messed up book. The first thing that catches your attention is that there are a number of page numbers in a book. Even if you don't understand a book written in another language, you can order it using the page number.
In the desktop computer world, this happens; The transport layer doesn't have a proper understanding of a message's information and its information model, so it can't understand and organize it properly.
For this reason, a sequence number is considered for each segment and the Segment Sequencing process will be able to correct the order of the received segments by placing the numbers next to each other.
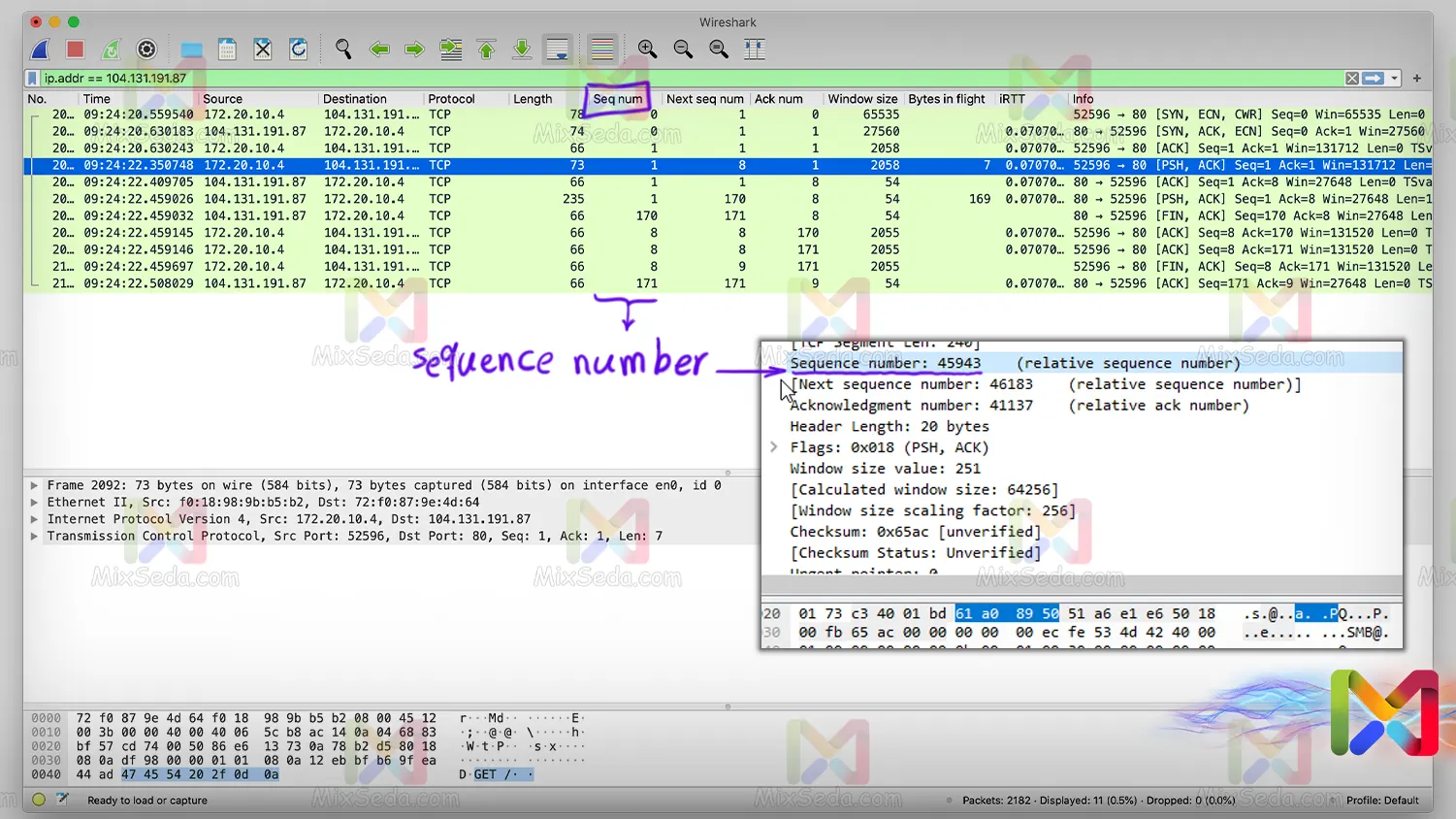
You can see the sequence number of each packet in the network using software like Wireshark.
Service Addressing
Imagine that in the real world I am sending a letter to the head of a department of a large company. After the letter arrives, the address on the package, the appearance of the package is checked, and if the package is faultless, it is delivered.
The parcel of the letter was opened by the secretary of the company and since it is written on the letter, which person in that company will receive this letter; The consignment letter is handed over to the head of the department head's office. And finally the letter arrives at its destination.
In the world of computer networks, the reception and verification of the correctness of the address of each packet takes place from the first to the third level. As mentioned, this is done via MAC address and IP address, which I have explained to you in this article.
But the problem is that the package has reached the destination computer, but it is not clear who it should be delivered to. Also, the transport layer lacks the literacy to understand this received packet.
For this reason, one of the things the transport layer does for us is use a label on each packet to specify which part of the destination computer this packet should reach. This process is called Service Addressing.
How exactly this process is possible, in the Cisco courses, you will cover exactly these topics and, for now, you will not need to know in the Network plus course.
In fact, each service in the upper layers of the OSI model, such as the application, is mapped to a number in the transport layer. And when information is received in the Transport layer, the information is delivered to the Service section in the higher layers.
For example, if you request to open a page in your browser, after receiving and reaching the transport level of the destination server, this request will be sent to a service assigned by default with the number 80 or 443.
Famous transport layer protocols

TCP
TCP or Transmission Control Protocol is one of the existing standards for establishing and maintaining communication between computers. A packet does not use a single protocol for sending over computer networks. In fact, each packet uses different protocols to send to reach its final destination.
TCP protocol also always uses IP or internet protocol to communicate. A lot can be said about the structure of TCP and the packets that are sent using this protocol.
In this protocol, a communication is established to send any information and until the information is completely transferred and the receiver sends the information receipt message to the sender; The connection is maintained.
Actually, when you want to download a file, you use the TCP protocol because all the information is important to you. Imagine downloading a piece of software; If any part of this software is downloaded incompletely, in most cases you will not be able to install it.
In general, the TCP protocol is used in cases where it is important that accurate and correct information reaches the destination. Imagine that for whatever reason there is a problem sending a packet and this packet does not reach its destination correctly.
Here the TCP protocol is in charge of identifying and fixing the problem in the received packet. In fact, this protocol drops the packet and requests the sender to resend the same packet.
On the other hand, this protocol sends an acknowledgment message to the sender, regardless of the number of packets received. On the sender's side, after sending any number of packets, TCP waits for a response.

UDP
Session layer
The session layer in the OSI model has three important tasks for sessions or work sessions in computer networks. In fact, as can be seen from the name of this level, the task of this level is related only to Sessions.
Imagine that you are performing an operation on the network. In the first stage, you need to create a session for this activity. So the first task of this level is to create or start a session.
The second task is that the created session must be maintained. You certainly don't want your connection to the service provider's server to be dropped in the middle of important activity; Because of this, the next thing this layer does for us is to maintain the created session.
The third reason you'll need this layer is to destroy created sessions. In computer networks, creators have tried their best to make everything happen based on some logic.
Do you think it makes sense for a Session to always remain open once created?
In addition to security issues, this could also increase network traffic. So the best thing is that when a session is created and an operation is performed in the network; When the session ends, the session is closed or session termination occurs.
In addition to the operations I explained above, the Session layer is responsible for checkpoints. In face-to-face and online classes, when a teacher or lecturer teaches you something, does she ask if you understand?
This question means whether you got all the information she explained and understood or not…
Checkpoints also have the same meaning in computer networks. Imagine two computers exchanging thousands of packets with each other. Of course, to transfer a large file, this number may be very small.
For example, when you back up from a server and store it on other hardware in the network, your network traffic will be much more than these words.
In this case, Check Point is responsible for checking each specific number of packets sent, with the destination computer to ensure that all packets have been received correctly.
Indeed, in the Session level, it is verified from which of the Check Points the destination computer received the information. Imagine downloading a movie to your browser. What is very common in Iran is that you may have problems with internet interference for various reasons.
Or for whatever reason, the session created between you and the server you download from is terminated. In this case, if you connect to the server again, you don't need to download the file from the beginning.
The provider's server can provide information from the last Check Point onwards. This increases the speed of computer networks.
Famous Session layer protocols
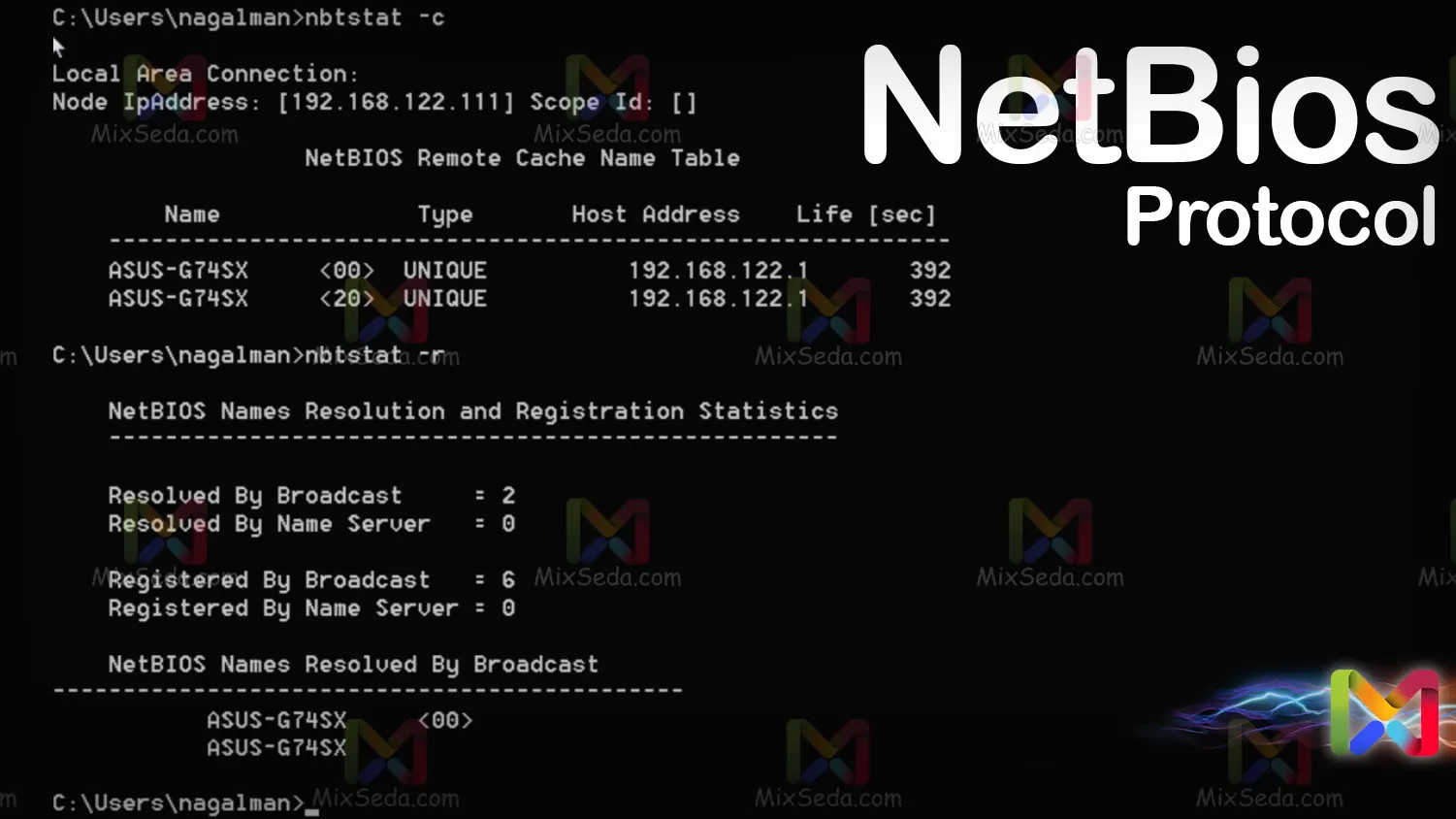
NetBios
NetBios is a very old protocol and you actually used NetBios before the TCP protocol was created. Actually, if we talk about NetBios today, we mean NetBios over TCP.
I mean, NetBios has used other mechanisms for sensing and communication in the past, which you can read about on the internet if you like.
NetBios was a protocol for communication between different computer programs. Of course, today NetBios is no longer used in standard networks.
Therefore, a common saying among network hackers is that if you've managed to find a network where NetBios has been used, you've probably hit some interesting places because NetBios isn't used as standard.
Typically, one of the tasks network administrators do is to close NetBios-related ports in computer networks. In fact, this can make your network computers more secure.
If NetBios is active in a computer network; You can use it to find out the names of computers, some services, etc., which are important information for hackers in a network, which is why scanning NetBios is considered one of the activities of hackers.
As far as I know, all older operating systems support NetBios. New Microsoft operating systems also support this protocol for communicating with an older computer. But on newer Linux operating systems you will no longer have NetBios.
If you have seen this, it is usually recommended to always disable or block TCP protocol ports 138 and 139 and UDP protocol port 137 in operating system firewalls. These ports are related to NetBios.
The NetBios output includes a table where the NetBios name and the service ID are present. Indeed, through NetBios, you can find out the names of computers and the services they provide in the network.
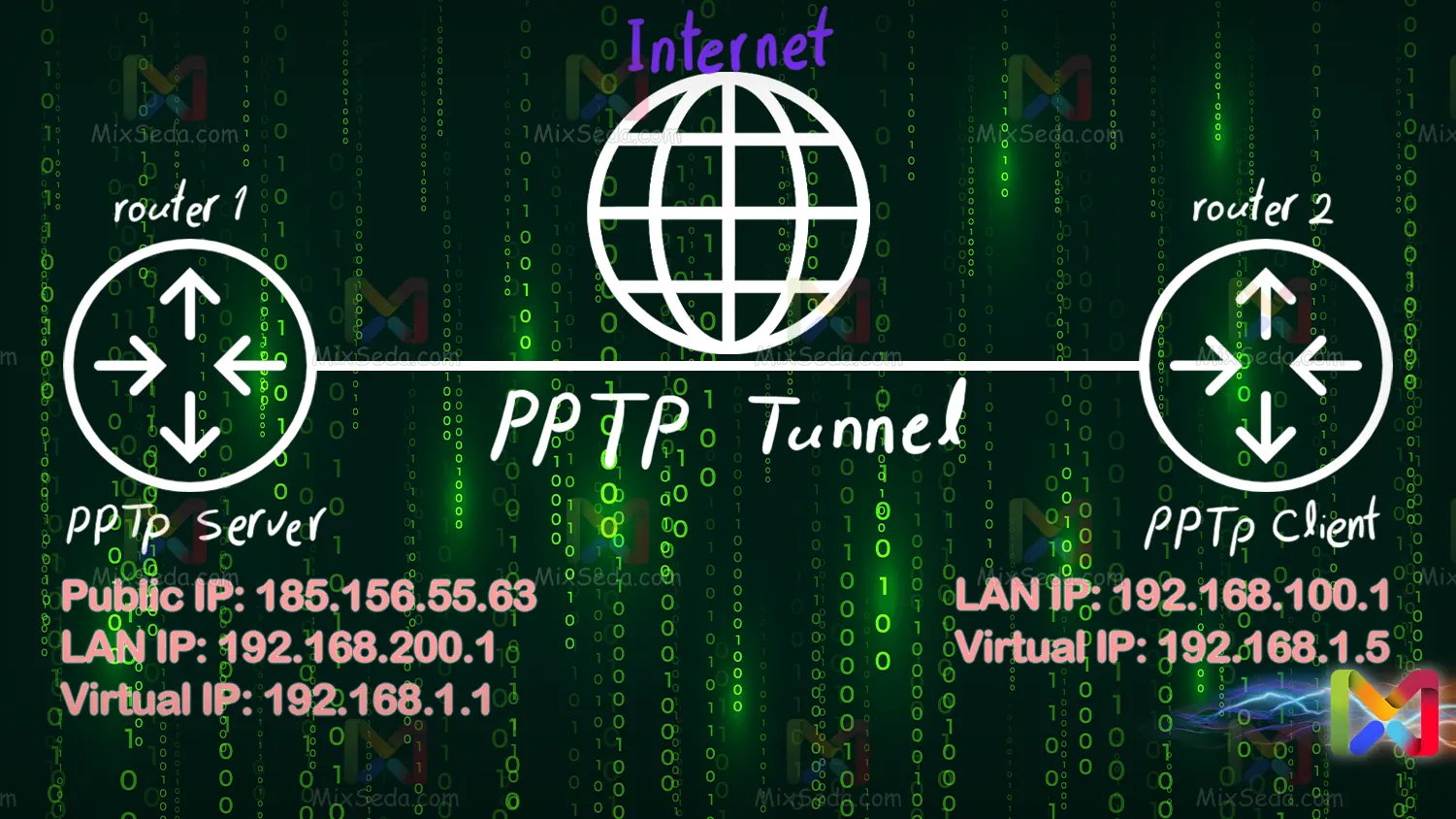
PPTP
PPTP or Point-to-Point Tunneling Protocol is one of the VPN communication protocols in computer networks. Naturally, this protocol is not used due to security concerns in standard networks and usually the L2TP protocol is used instead of this protocol.
This protocol was designed in 1999 by several companies, including Microsoft, and has shown outstanding speed and stability across protocols. PPTP was mainly used when two routers needed to communicate directly with each other.
PPTP is one of the simplest protocols available in terms of structure, but in terms of confidentiality of the information sent by this protocol, it has known weaknesses.
The reason for the low security of this protocol is that PPTP uses RC4 encryption, which has known vulnerabilities. For this reason, this protocol is currently only used in cases where security is not important.
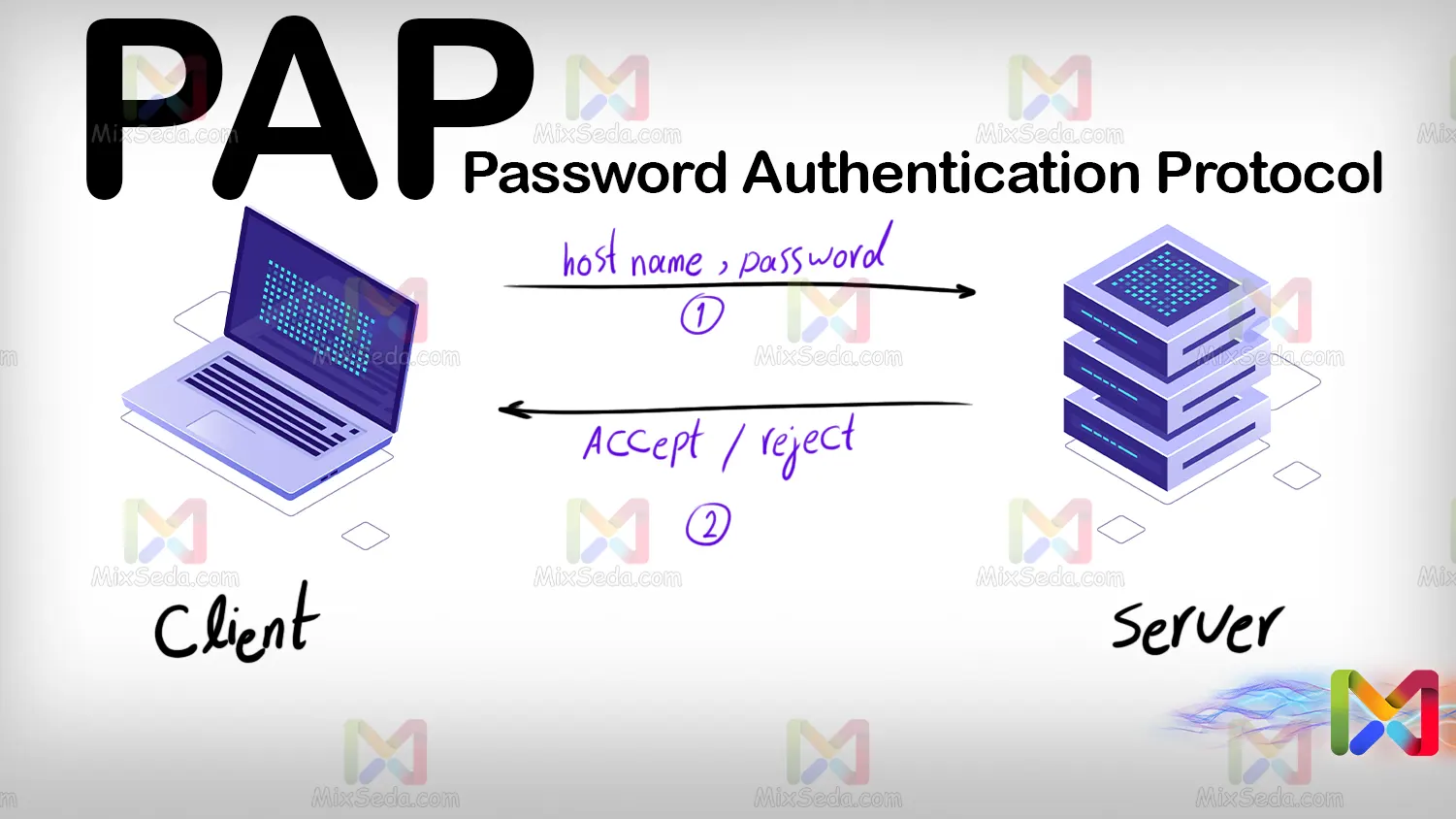
PAP
PAP or Password Authentication Protocol is a security protocol for password authentication in computer networks.
There are protocols like PPP whose job is to establish a secure remote connection. These protocols cannot work independently and need other protocols to authenticate users to perform their tasks.
In the past, there was a protocol called SLIP or Serial Line Interface Protocol, which was used for password authentication, but over time, this protocol was abandoned due to its weaknesses and the PAP protocol replaced it.
After establishing a connection between a client and a server using the PPP protocol, the client's computer uses the PAP protocol to send sensitive information such as username and password.
Of course, today this protocol is not used in a standard network, because this protocol causes a number of security problems. One such problem is that the PAP protocol sends user information in text format.
This allows a hacker in a computer network to easily extract sensitive information without any problems and use it for his own purposes after hacking into the network and listening to the information.
Usually, in standard networks, they try to use protocols that send sensitive information encrypted. Indeed, now that new news about hackers is heard every day, the concern of most companies is to maintain security.
Presentation layer
One of the most important tasks of the presentation layer is to perform encryption and compression operations. Imagine a series of packets being sent across your network as Encrypt. In this case, the sender's presentation layer performs the encryption process for each packet.
And on the presentation layer side of the receiver, the received packets; It is decrypted and then delivered to the top layer i.e. Application.
The same thing happens with the compression process; If we say that the presentation layer performs the compression, on the other hand, the extraction process takes place so that the received packets can be understood by the application layer.
In this level, the packets sent and received are called a message. In general, in the first three layers of the OSI model, namely Session, Presentation and Application, the type of information is given and the packets sent and received in these layers are called messages.
In some sources and articles related to computer networking, the presentation layer is also known as translation.
Famous Presentation layer protocols
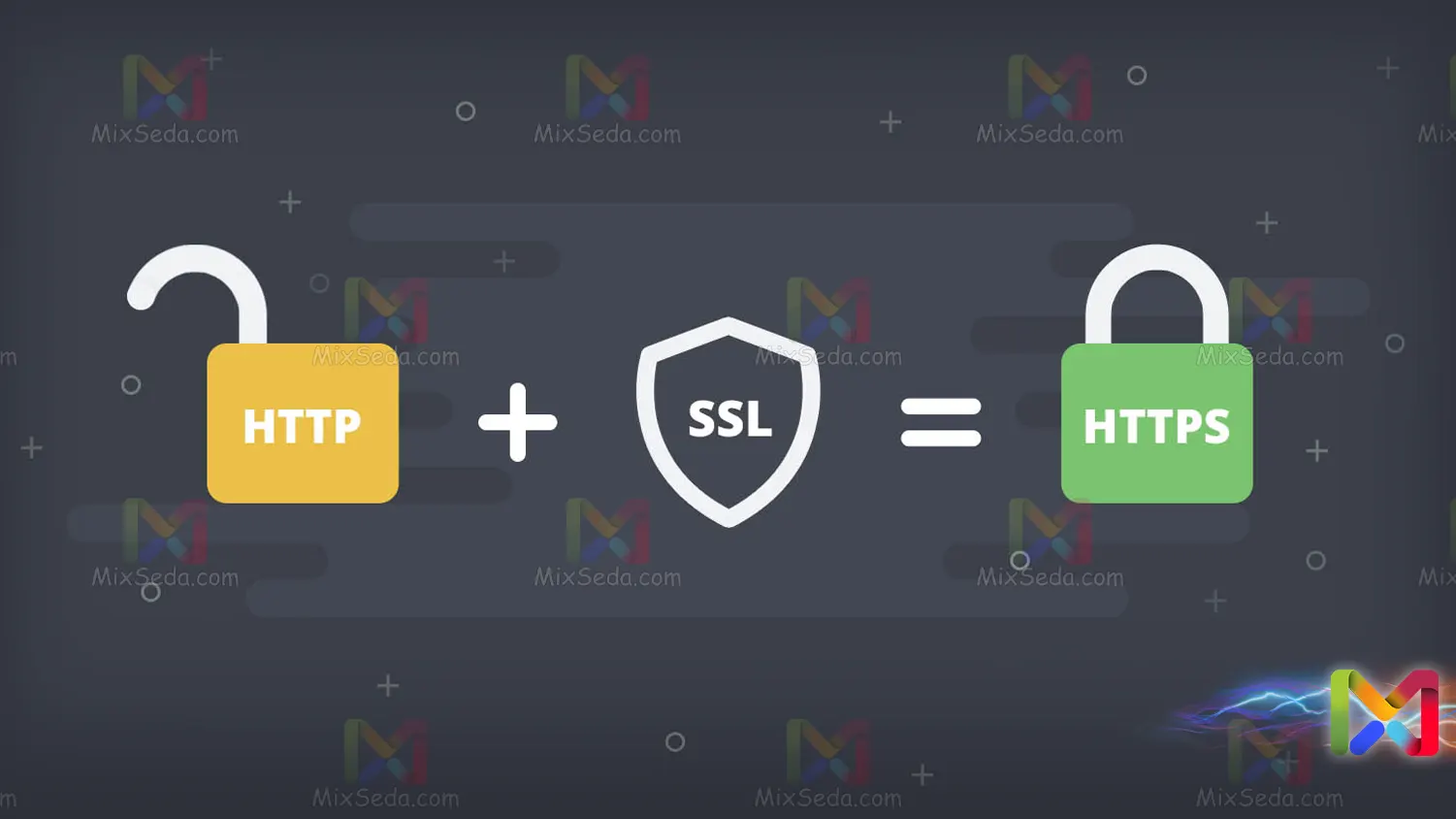
SSL
The SSL or Secure Socket Layer protocol was a protocol for establishing a secure connection between the server and the client, which was introduced by Netscape in 1994. Of course, in the initial version of this protocol, no one was willing to use it due to security bugs.
But with the release of the second version in 1995 and the third version in 1996, the situation was somewhat different. SSL provides security and users use SSL for both security and privacy.
However, when you create a site, you get an SSL certificate for it. You actually think you are getting an SSL certificate.
The second version of the SSL protocol was deprecated in 2011 and the third version of this protocol in 2015. The story here was that this protocol was so old that using it caused security problems.
In fact, if you are currently getting an SSL certificate for your website, your site uses the TLS protocol for secure communication. In 1999, the first version of the TLS protocol was released as an update to the SSL v3 protocol.
The SSL protocol uses several algorithms, including asymmetric encryption algorithms, to create a secure connection. Explaining these algorithms and how each of them works is time consuming.
After providing different versions of SSL protocol, many other protocols such as http, SIP, SMTP, POP3 and FTP have used this protocol to create security in sending and receiving information.
Using the SSL and TLS protocols requires that both the client and the server have digital certificates. For this reason, a number of digital certificate issuing centers (Certificate Authorities) have been created.
The task of the certificate authorities or CAs was to know the identity of the communication parties, account information, certificate expiration date, etc. and authenticate computers based on the cases recorded in it.

TLS
The TLS or Transfer Layer Security protocol, as I explained above, was one of the versions of SSL. In 1999, the first version of the TLS protocol was introduced. In 2006, version 1.1 of this protocol was released on the market. Today, the TLS protocol is used for the following applications:
- Ensure the correctness of the data sent and do not change the information
- Ensure the authenticity of the identity of the parties exchanging information
- Ensure the security of information and the lack of third party access to the information exchanged
In TLS, three main things happen that provide us with the security of information exchange in networks. As I explained to you in the SSL protocol, we needed a set of certificate authorities or CAs to issue digital certificates.
Now, in TLS, the identity of the server and client is first confirmed using a certificate. In fact, the first thing that happens is that the Client checks if the Server providing the service is who it claims to be.
Then the service provider's server verifies the client's identity using its certificate. If these two steps are performed correctly, the server and client exchange information using special encryption.
Application layer
As I explained above, this level is the level closest to the user. In this layer, communication between users and the network is established, and application software such as browsers and network communication tools operate in this layer.
The application layer is also called the user interface in some articles. In fact, since this layer is the layer closest to the user and all user requests are created directly on this layer, it is also called the user interface.
The application layer is specifically related to software and tools programmed by programmers to operate in computer networks.
For example, all software and tools like Wireshark or even social networking software like WhatsApp etc, that operate on the network are basically placed in the Application layer.
Note that the OSI layers relate only to protocols, tools and software that operate in computer networks. For example, a Notpad software falls into none of the OSI layers.
Or, for example, Microsoft Word software is not found in any of the OSI layers, but if you were faced with Word software that stored your files in cloud storage, this software can be said to operate in the Application layer.
Don't think that any software that works on a computer definitely works in one of the OSI layers. One of the events that occurs in the application layer is the initiation of the request.
Request initiation means that one of the tasks at this level is to create a request. Imagine opening a browser and searching the internet for a word. Or you want to connect to another computer via SMB protocol and check its File Sharing.
In all these cases, you create a request and since the user creates all these requests, basically these requests are created on the seventh layer, Application.
Or, for example, when you open a web page, you actually use the Http protocol to open a page. Application layer communication packets are called Message. After creating a request and producing a message, these packets are sent to the lower level, i.e. Presentation.
Famous application layer protocols
FTP
FTP or File Transfer Protocol is a very famous file transfer protocol. This protocol is one of the most used protocols and its job is to transfer files from one host to another.
You can use the FTP protocol when you plan to transfer files between the server and client over the network. Prior to this protocol, other methods were used to transfer files to a server.
For example, information was placed on a floppy disk and transferred to the server. In 1985, after the standardization of the FTP protocol (RFC 959), FTP was used to transfer data.
FTP allowed users to download and upload to servers. Also, it was possible for users to delete or create a directory or folder and report files on the system.
Other features of this protocol include file deletion, moving and searching, which made the FTP protocol more popular. The FTP protocol can be accessed using the following three methods:
- Operating systems terminal or Windows command line
- Browsers
- FTP client software such as File Zilla
Of course, the FTP protocol also had some shortcomings, among which we can mention the lack of data encryption between client and server. For this reason, SFTP or SSH File Transfer Protocol is used in networks today. In the rest of this article, I will explain more about the SSH protocol.

http
The http protocol or Hyper Text Transfer Protocol is a standard protocol for exchanging information in computer networks. After the birth of the first sites, the http protocol was created which allowed users to transfer information.
Before the http protocol was created and introduced in 1991, there was no standard method for exchanging information in computer networks.
Despite this protocol, information transfer was not limited to text and images only, and http provided audio and video transfer facility for users. In addition, other protocols such as FTP have also been able to work using the http protocol.
We can talk for hours about how this protocol works, but in a very simple and concise way; When you open a web page, you send a request to that website's server.
As a result of the request sent by each client, a response is sent from the server side. Your requests can be of different types. All these things are events that happen in the background and their result is the opening of a web page in your browser.
Each request message sent from the client to the server includes a request line, header, and body. And each response message sent from server to client contains status line, header and body.
In CEH courses you will learn about all these components, also learning Http request types is mandatory in network security courses. But considering you aren't familiar with many concepts yet, learning these parts won't help you.
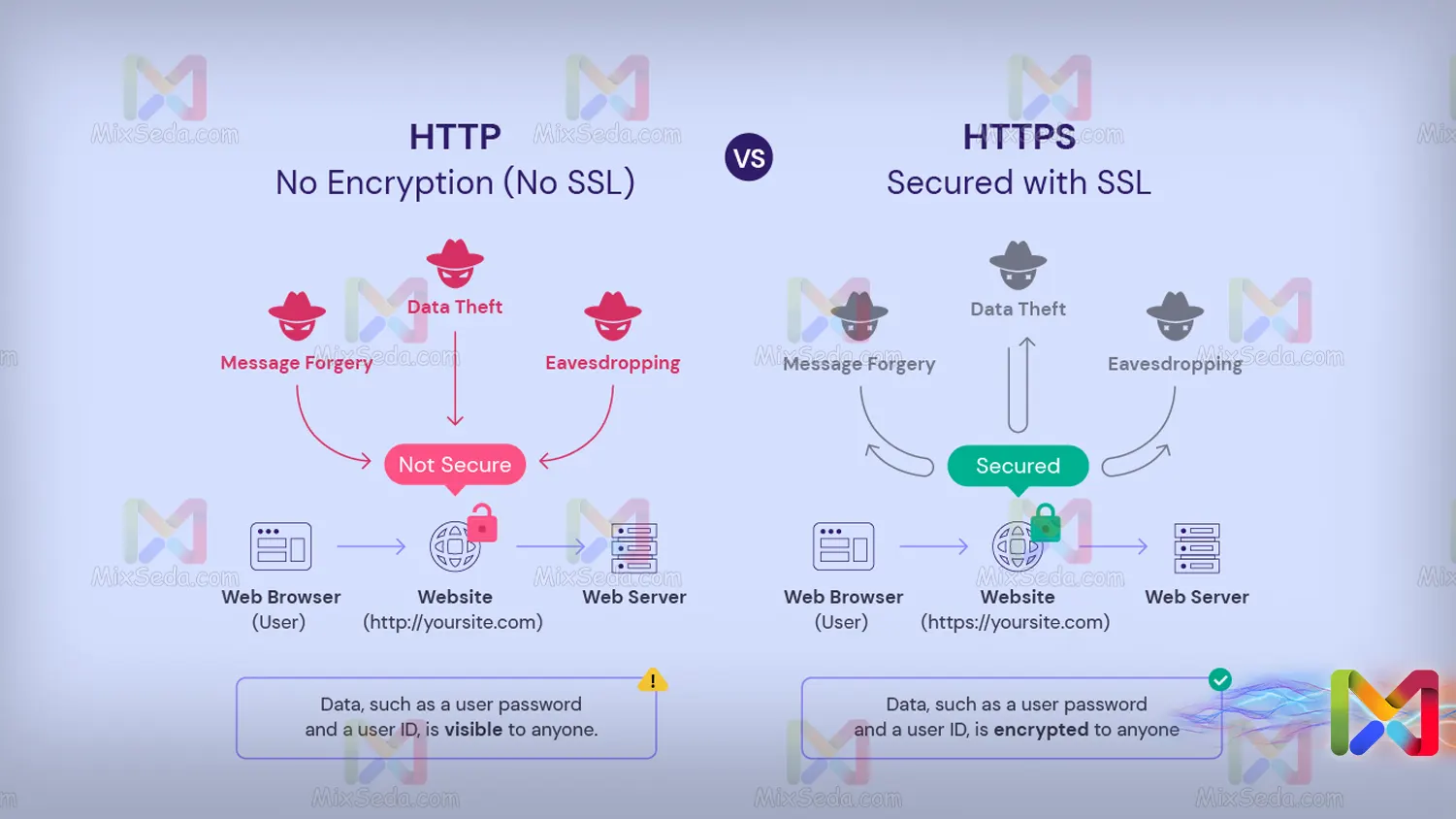
The Http protocol also had problems, among these problems it can be mentioned that the communication is not secure. You must have heard that you shouldn't access sites that use http. In the http protocol, in fact, no measures have been taken to secure communication.
In a computer network, a hacker could easily notice the information that is exchanged between the Client and the Server with the Http protocol by listening to the network. For this reason, protocols such as SSL and TLS have been used to secure this connection.
The story wasn't limited to hackers; In many countries, such as the United States, ISPs or Internet Service Providers could track user information and sell it to advertising companies.
For this reason, users had to resort to the Https protocol to protect their privacy. It makes sense that nobody wants others to know what they are doing on the Internet.
Indeed, the Http protocol was combined with SSL and the result was the Https protocol, which ensured the security of information between Server and Client using a certificate. Because of this, neither the hacker nor anyone else could notice the received and sent information.

POP3
POP3 is one of the most popular email sending protocols in computer networks. POP3 or Post Office Protocol is responsible for sending an email to the destination.
The point is that after the email reaches the recipient, this protocol drops the message from the POP3 server so that no further information about the message is available on the servers and this is actually done to increase security.
As for the POP protocol, what you should know is that newer versions of this protocol have been created and provided, however, the POP3 protocol is very famous and is still used by many users in different networks.
There are other protocols for sending email to the destination. For example, one of these protocols is IMAP, which has a more complex structure and mechanism than POP3. But what made the POP3 protocol famous is its ease of use.
The function of POP3 is that email senders send their messages to POP3 servers and the server temporarily stores the emails in itself and waits for the users to connect.
After the computers connect to this POP3 server, the server sends the messages to the recipients and deletes them from the server after making sure that the email has reached the correct destination.
Despite the popularity of POP3, nowadays in computer networks, people try not to use this protocol because it has many disadvantages. Indeed, since this protocol is obsolete, it has many security problems and configuring it in a network can endanger user information.
Usually people try to use IMAP protocol instead of POP3 protocol for email in networks because this protocol is more secure than POP3. Furthermore, the existence of a number of services and benefits in the IMAC protocol increases the security of emails.

SMTP
SMTP or Simple Mail Transfer Protocol is an older protocol for transferring email. This protocol is an older protocol for sending email from one account to another. Of course, other protocols such as POP3 and IMAP are also used for email.
When you send an email, you are actually connecting to a mail server. This SMTP server is responsible for sending your email to its intended destination. Now, if your destination is in the same network, this SMTP server will send your email directly to POP3 and IMAC servers in the same network to reach the destination.
If your email destination is not in the same network, the SMTP server must deliver your email to another SMTP server in another network so that the server can send your email to the destination.
For example when you send an email to info@mixseda. com, your SMTP server forwards your email to the mixseda domain's SMTP server. com offers. Meanwhile, the SMTP server of the email sender needs to ask the DNS server for help to identify the SMTP server of the email recipient.
After the email reaches the destination SMTP server, this server delivers the received email to IMAP and POP3 servers so that these protocols deliver the email to its intended destination.

IRC
The IRC protocol or Internet Relay Chat is an old protocol for transmitting messages over the network. In the past, social networks weren't as powerful and accessible as they are now. Therefore, the IRC protocol has been used to chat with others.
The IRC protocol was created in 1988 by Jakko Oikarninen. You will be able to connect to an IRC server using this protocol. In fact, IRC clients are authenticated using their nickname, username and IP address on the IRC server.
To use this protocol, you need IRC client software. For example, mIRC software used to be one of the most popular software for connecting to an IRC server.
In fact, what you see today in many messengers was first introduced to users by the IRC protocol.
Even in some IRC servers, voice calls, video calls, file transfer, conferences, etc. are also available for active users. You can communicate with other users using this protocol.
Early messengers used a combination of the IRC protocol with a number of other protocols for file transfer or other functions. I can easily say that the creation of this protocol in 1988 was indeed considered a great achievement.

SSH
The SSH or Secure Shell protocol is a framework and mechanism for secure communication created in 1995 by Tatu Ylönen. Tatu Ylönen created the SSH protocol to improve communication over the Telnet and rLogin protocols.
But he protocol was so well designed that later this protocol was also used to secure other protocols. In a very simple way, this protocol encrypts information on the source computer using the RSA algorithm.
The existence of encrypted information in the network read made it impossible to use if that information was intercepted or subjected to MITM attacks.
MITM stands for Man In The Middle; It is one of the attack methods in computer networks widely used today.
If you do not use encrypted information between your computer and the desired server, and a hacker listens to the information, he can easily find out this information.
Of course, if this information is encrypted, it is also possible to crack the password by finding the private password of the computers, but in any case, the security is better using the SSH protocol.
Obviously this protocol, like many other protocols, has many weaknesses, and usually network administrators try to have more secure SSH connections by applying a series of restrictions in the firewalls.
For example, in some networks, they change the port number of the SSH protocol. Or sometimes it is determined on network firewalls that only specific IP addresses can use the SSH port to increase the security of this protocol.
If you want, you can learn more on the Internet about how the SSH protocol was created and how port 22 was assigned to this protocol.

DNS
In computer networks, a DNS server or Domain Name System server is required so that computers can ask their queries from this server.
You may not have much information in the real world. For example, you don't remember all the phone numbers, and to find a phone number for a public place, you can call 911.
The same thing happens in computer networks and your computer has to send a request to its DNS server to know a piece of information in the network.
Your DNS may not know the answer to this question and has to ask another DNS server or send you to another DNS that knows the answer to this question.
The DNS server has three important tasks in computer networks and I will explain each of these tasks in a future article:
- Convert FQDN to IP
- Convert IP to FQDN
- Service Locator
A lot can be explained about DNS. Indeed, DNS is one of the topics you can discuss for days. Also, if you've entered the world of security and are familiar with attacks using DNS, you know that DNS is one of the most important and fascinating discussions in the web world.
By default, a DNS server uses port 53 to serve clients.

Network Admin & Engineering
In some job interviews you may be asked what is the difference between Network Admin and Network Engineering. It is possible to classify the OSI layers according to the type of information they contain and their functions.
This is also a type of OSI layer classification. The network administrator understands the first three layers of the OSI model. In fact, Network Admin includes Application Layer, Presentation Layer, and Session Layer, which administrators are usually responsible for managing.
In the CCNA and CCNP courses, which are Cisco courses, the focus is on the first four levels of the OSI model. These layers are communication layers between workstations and the people working on these layers are called Network Engineering.
Indeed, in Network Engineering, a platform for communication in computer networks is created, but the three upper levels, i.e., the levels of administration of the network, determine the purpose of communication.
